Tech Support Scams – Don’t Be A Victim
“Hello we have been notified your computer is infected. I’m a Microsoft Tech calling to fix it for you.”
Sound familiar? I hope not, but it’s a scam that’s spreading and many people are being drawn in and taken every day. So much so that this kind of tech support scam has grown into a million dollar industry.
Tech support scams were first reported in 2008 and sadly every day victims are being tricked into spending hundreds of dollars on non-existent computer problems.
There are two versions of this scam, the first is a call to you from a fake “Microsoft” technician. The second involves the victim calling in for “premium” tech support or product registration / activation from a dishonest company.
The calls from a “Microsoft” technician often originate from overseas call centers, most frequently reported to be India and typically are targeted at the United States, Canada, the UK and Australia. The scam itself is fairly straight forward. Trick whomever answers the phone into believing they have something malicious running on their computer, over act a bit to hype up the victim’s fear, gain remote access and trick the victim out of money. Beyond getting your money some of these will also install malware onto your system. As if paying for fake tech support isn’t enough you may also have your identity stolen.
Calling in to so called “premium” tech support, or being transferred from a reputable company to somewhere else for product activation, works in a similar manner. Say your computer is slow so you Google “computer slow” and you find a number of companies offering solutions. The dishonest “premium” support companies advertises heavily on the all the major search engines, as well as advertising on websites, so you’ll be sure to find some listed there. You call in to a company that looks like it’s a good price and will solve your problem only to have the same methods used on you to bilk you out of more money for phantom problems or have malware installed.
Another version of this comes from larger companies who send you to these tech support companies to activate some software and by the time you’re done you’ve spend hundreds of dollars to “fix” the other problems the tech support has found.
How do they trick people into believing their computer is infected?
The “Microsoft tech” tells you they’ve been notified your computer is infected and they need remote access to your computer to fix it before the problem gets worse. Remote access is when a tech logs into your computer from an offsite location to perform work on your computer / server. (This is the moment to just hang up on them.)
Once remote access is allowed these techs use a variety of methods to trick you into believing your computer is at risk and needs immediate attention. Their goal is to make you believe you have errors, viruses or malware running wild on your computer. To do this they often use the default Windows tools against you.
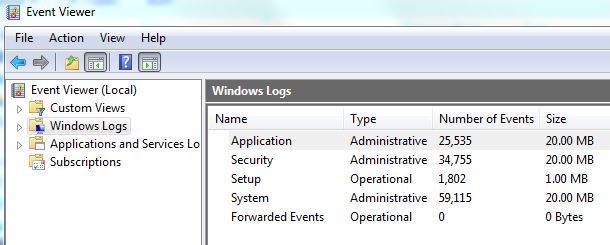
One tool they use is the Event Viewer. The Event Viewer is a central location for all of the log files from your computer. It is used by techs to diagnose specific issues. If you were to go look at your Event Viewer, as these guys want you to, it looks like you have all kinds of problems going on. Here’s an example of an Event Viewer:
That can’t be good right, this person has 34,755 Security events!!! Well actually if you look in the log, the vast majority of those “events” are logons and logoffs. But if you don’t know that and the “Microsoft tech” gasps and says “34,755 events this is terrible!”, most people are likely to believe him.
Another tool they use is the System Configuration Utility , which will show some programs are “Stopped”. It is perfectly normal for some services to be stopped and having certain start up programs disabled can actually increase the efficiency of your computer at boot up. Task Manager is another weapon they use by showing you CPU spikes and then proclaiming them to be highly dangerous or going to cause irreversible damage. CPU usage varies depending on what is or is not running.
Other tools they use include finding “critical” errors in the System Information, temporary files that can’t be deleted, fake scanners aka fake antivirus programs to make you believe you have viruses, open DOS prompts and run a variety of commands that really show nothing other than system information but they claim it’s showing malicious items, actually faking information directly in the DOS prompt, running a “ping” test to an IP address they know will fail, showing that your Network Action Protection is disable (this is normal for computers that don’t attach to a domain), and opening files in Notepad that shouldn’t be opened there so it looks like gibberish.
All of these tools are used to trick you into agreeing to pay them for support you don’t need.
What to do if you’ve been scammed?
First if you’ve found this article and are still on the line with them hang up now and cut off their remote access. If you’re unsure how to cut their remote access, the sure fire way is to restart your computer.
If this is a call you’ve received previously, whether you stayed on long enough to pay them money or not, there are several places you should report them to. File complaints with the FTC, Fraud.Org the National Consumers League, your local Attorney General, and if you’ve been defrauded of money your local law enforcement as well. Fraud.Org is an especially good one to file with as they work to share information with many jurisdictions. Local law enforcement is harder as they really only deal locally and scams like this work on a global scale not a local one.
You will also want to have your computer checked out by a local technical company in case anything malicious was installed on your computer during the so called technical support.
Remote access tech support is a great tool when it comes to troubleshooting computers and servers as long as it’s in the right hands. If you’re getting remote support from a local company, with a brick and mortar store front, you’re unlikely to be scammed. Scammers are working in large overseas call centers or on US soil more likely to be working out of their mom’s basement.
Also keep in mind that many of these not local scammers are using technology to fake local numbers on caller ID numbers when they call you. It is always advisable to do business with a local computer company, but make sure that local number really leads you to a local company.
[whohit]TechSupportScam[/whohit]



1 Comment
I’ve had these people call me 3 times in the past 2 days. I already knew they were scamming. I asked the first one what their phone number was and got an 855 number. I could pretty much tell they were calling from India but when I asked he said California. So I asked what time it was there. He gave me a time that was 3 hours off! The second one (same phone) told me Salt Lake City, California. After 5 minutes or so, he asked me why I was still talking to him and I said because every minute you are talking with me you are not scamming someone else. Conversation went downhill after that.
The third one, spoofed local number, I was out of time. I told him he was scamming me and he should get a real job.
Thanks for the article though. Quite informative.